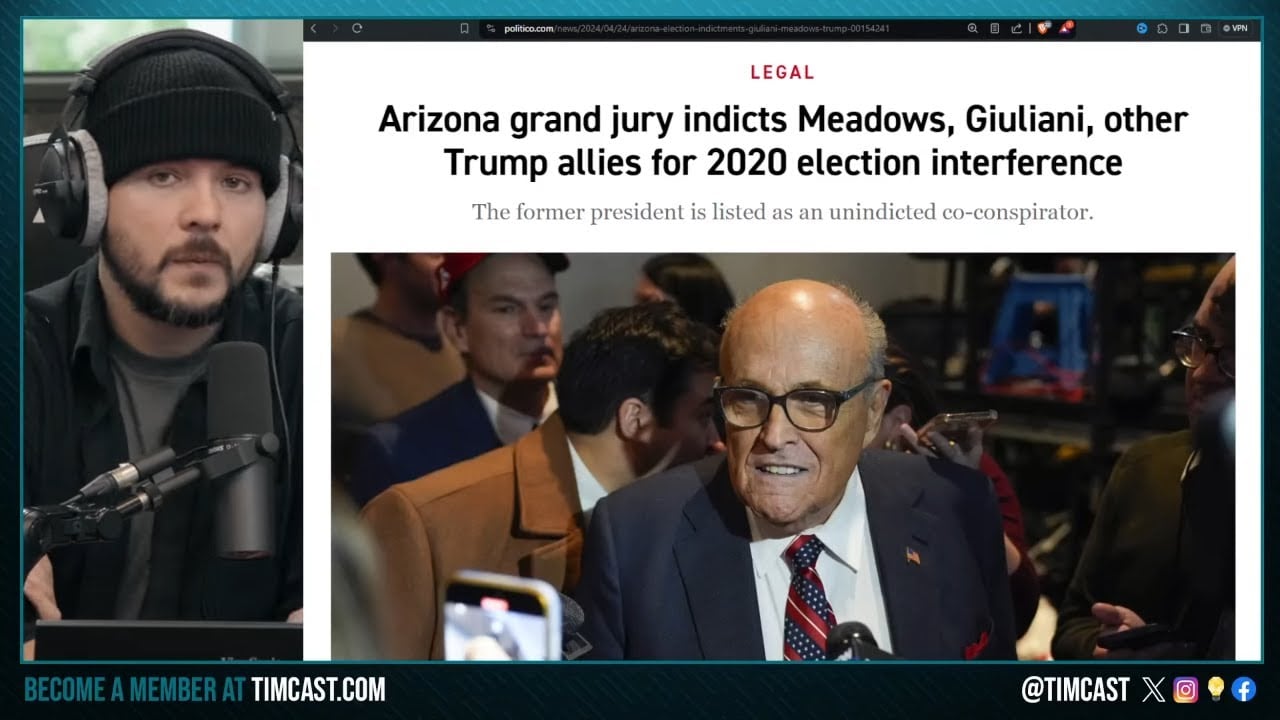
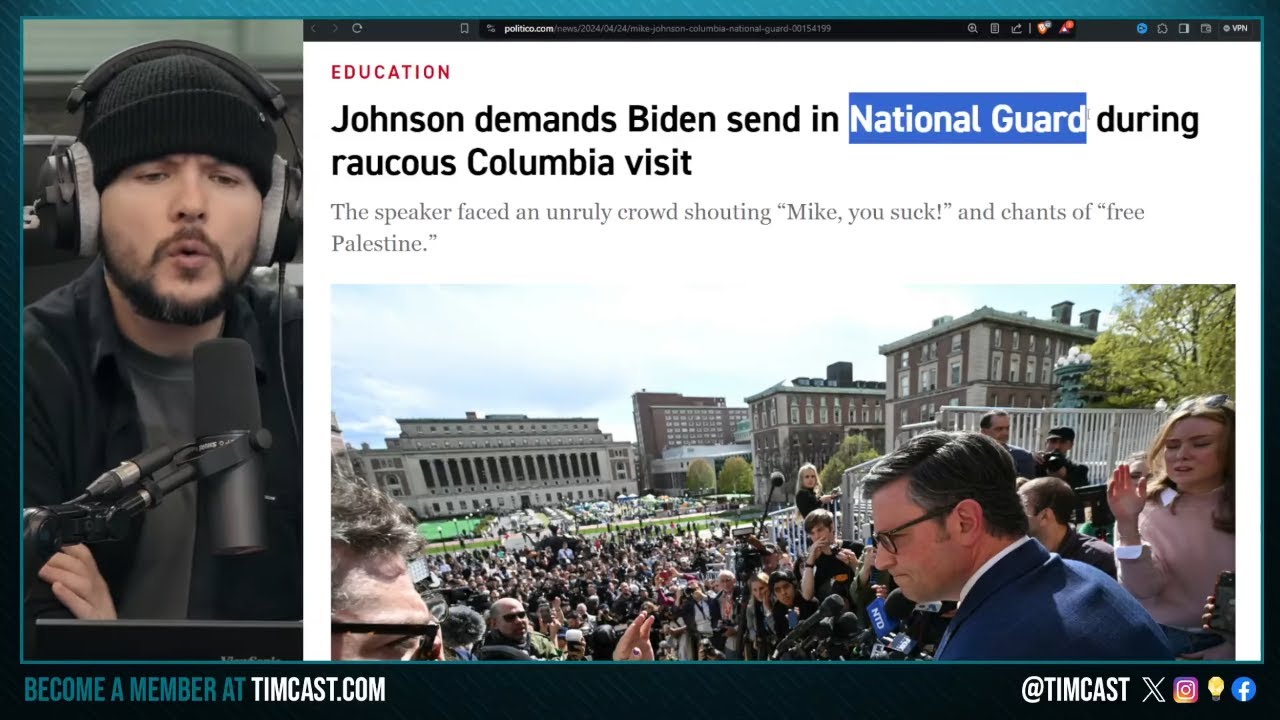
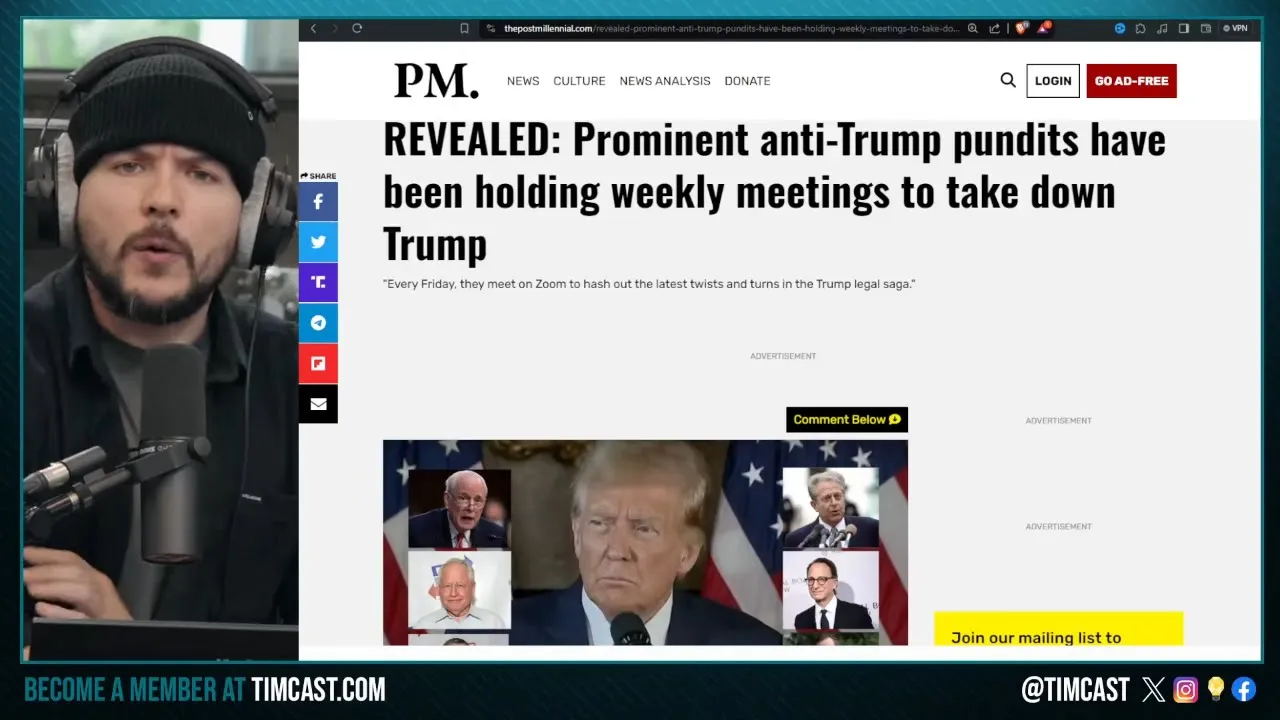
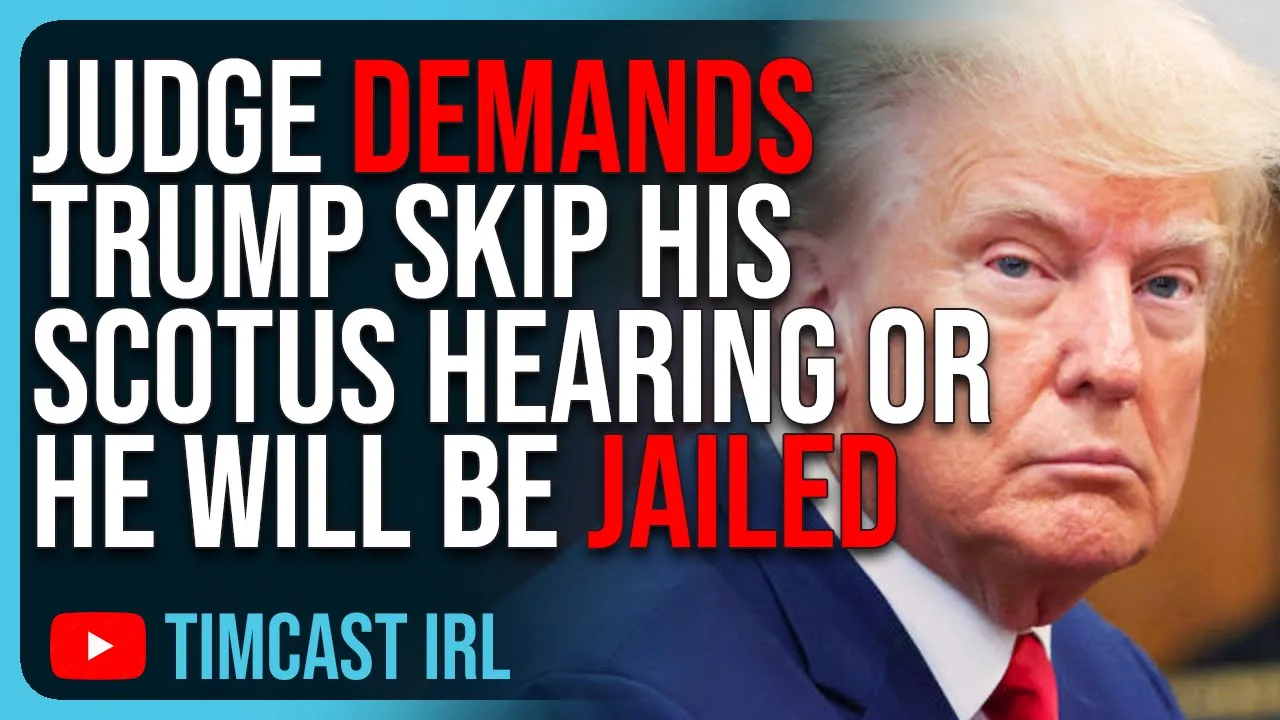
#AmericanJournal HR1: Anti-Trump Murkowski Trails GOP Challenger by 15 Points
The American Journal (Hour 1) - Commercial Free - 4-6-21
The purge of RINOs begins!
Share across all globalist controlled platforms. Do not keep them on safe platforms because most people on those platforms are already awoke to the lies of the New World Order agenda! If you do not share this becomes an echo chamber.
💲 SUPPORT/DONATIONS 💲
Fighting to keep all truth on banned platforms like Youtube/Twitter/Periscope etc. If you want to continue see truth on these banned platforms please consider subscribing so you can help fight the good fight.
• If you can. please donate to:
• Cash App - http://bit.ly/2Q0rXcq
• Bitcoin - 1DDZeUG2As6t9V8b9JLJDLefddJffiJbKW
• PayPal - https://bit.ly/36Uyuhf
◄◄ Subscribe to my Subscribestar account if you can do a monthly donation! ►►
• Subscribestar: - http://bit.ly/35YelE5
📡◄ Follow Me ►📡
All the platforms and donation links are accessible using the URL below:
• https://linktr.ee/TheResistance1776

And The Commander Spoke…,
The Whole Wide World was shut down so CORPORATIONS and CAPITALIST could Upgrade all their {A.I. Security} and the PROOF too this can be seen, and read by looking at Johnny Exodice on mewe.com
In this’ all these people whom say we LANDED ON THE MOON, and their “children” are in on these LIES AGREED UPON, and only by [USE OF FORCE] Qballs~ /_\ will you ever get any honesty from the CEO’s and their family members: whom are “too blame” for so many of OUR nonmason GENTILE “deaths” since the end of the MUD FLOOD WARS where we nonmason GENTILE Populations are played with like TOYS in a Game,
and it is these FREE MASON (Lodges) / * \ and their FAKE JEWS from the BOOK OF REVELATION known as all connected to Hollywood TV Shows of Subjugation – Submission – Servitude to these [U.N. FLAGS] of CORPORATIONS whose command structure is a Pyramid Scheme with the Vatican Jesuit at the Top of the Pyramid,
the TALMUD ZIONIST of Hollywood and their S.A.T.A.N. Worship at the Bottom of the Scheme where Lucifer, and his {DEAD Light} +=+ has always been this EDISON A. I. Machine, below all others are FREE MASON INTERNATIONALIST, and their (Global Citizens) [{*}] with their Global Pass Ports for Agenda 21 and Agenda 2030 of the U.N. Troops of {G4S]
and it is “these” people who laid you off from work, or let you go, and now the #BITCOIN is just one more Trick or Treat for {a 2 Layer I.D.} /-\ Verification System for all INVADERS with their Black Dots for EYES…
Look at their EYES on these TV Screens, and then look at your [own eyes] in the Mirror and ask yourself this: how many #COVAXXED “Injections” need to be put into our Blood, and Bones, and Brains too make our EYES get covered by the BLACK GOO by all these Hypodermic Needles of (COVID19) .?.?.?.?
The Vaccines are destroying human {EYE Colour} and giving all people BLACK DOTS for eyes no matter how Light Your Skin, nor how Dark your skin…
Things you will ponder in this NEW REALITY where CORPORATIONS and (TV Shows) have always called all the shots with their MALFEASANCE where “masons” run the Supreme Courts, and none of these MONSTERS will ever go too Jail, let alone spend any TIME in Prison for what they have done to WE THE PEOPLE on this side of flat earth…
https://www.youtube.com/watch?v=VosA_rsfd78
Is PURGATORY nothing more then a Game.?.?.?.?, and {we are} nothing more THAN the Action Figures as [Pieces of life] on this: ALL THE WORLD IS A STAGE???????, if you are (not allowed) too have A say in the LAWS you pay for: with your MONEY called TAXES……., then you are “nothing” more then the word EMPLOYEE nonmason Gentile!!!!
And under the RULE of LAW and ORDER the word employee: does mean “SLAVE” in any, and all courts of LAW on this side of FLAT EARTH…
The Commander~ #TheCrewRRR [{**}]
---------------------------------
Another SolarWinds Orion Hack
At the same time the Russians were using a backdoored SolarWinds update to attack networks worldwide, another threat actor — believed to be Chinese in origin — was using an already existing vulnerability in Orion to penetrate networks:
Two people briefed on the case said FBI investigators recently found that the National Finance Center, a federal payroll agency inside the U.S. Department of Agriculture, was among the affected organizations, raising fears that data on thousands of government employees may have been compromised.
Reuters was not able to establish how many organizations were compromised by the suspected Chinese operation. The sources, who spoke on condition of anonymity to discuss ongoing investigations, said the attackers used computer infrastructure and hacking tools previously deployed by state-backed Chinese cyberspies.
While the alleged Russian hackers penetrated deep into SolarWinds network and hid a “back door” in Orion software updates which were then sent to customers, the suspected Chinese group exploited a separate bug in Orion’s code to help spread across networks they had already compromised, the sources said.
Two takeaways: One, we are learning about a lot of supply-chain attacks right now. Two, SolarWinds’ terrible security is the result of a conscious business decision to reduce costs in the name of short-term profits. Economist Matt Stoller writes about this:
These private equity-owned software firms torture professionals with bad user experiences and shitty customer support in everything from yoga studio software to car dealer IT to the nightmarish ‘core’ software that runs small banks and credit unions, as close as one gets to automating Office Space. But they also degrade product quality by firing or disrespecting good workers, under-investing in good security practices, or sending work abroad and paying badly, meaning their products are more prone to espionage. In other words, the same sloppy and corrupt practices that allowed this massive cybersecurity hack made Bravo a billionaire. In a sense, this hack, and many more like it, will continue to happen, as long as men like Bravo get rich creating security vulnerabilities for bad actors to exploit.
SolarWinds increased its profits by increasing its cybersecurity risk, and then transferred that risk to its customers without their knowledge or consent.
Tags: backdoors, China, cyberespionage, FBI, hacking, Russia, supply chain
Posted on February 4, 2021 at 6:11 AM • 36 Comments https://www.schneier.com/blog/....archives/2021/02/ano
-----------------------------
Companies must change the way they operate to combat increasingly sophisticated cyberattacks across ever-expanding attack surfaces. What we learn from one attack can help us protect against the next. Because the next attack is always on the horizon. What should you do to raise your defenses?
SolarWinds President and CEO Sudhakar Ramakrishna, cybersecurity expert and Krebs Stamos Group Founding Partner Alex Stamos, and Head Geek Thomas LaRock discuss our plan for a safer SolarWinds and customer community – grounded in principles you can follow to secure your enterprise.
Sudhakar addresses the steps SolarWinds is taking to:
Further secure our internal environment
Enhance our product development environment
Ensure the security and integrity of our software
Part of that work is drawing on the experience of cybersecurity experts like Alex – founder of the Stanford Internet Observatory, and recognized security technologist – who led security teams at Facebook and Yahoo through significant security challenges and continues to do so for companies like Zoom and SolarWinds.
Alex details what you can learn from this most recent cyberattack – and others like it – to change how your organization operates.
Learn to audit your cloud trust relationships
Learn to build for code integrity
Learn to centralize your monitoring to accelerate detection and speed response
Learn to document network dependencies to better control access
Learn to enhance permission rules and risk-based authentication
https://orangematter.solarwind....s.com/2021/02/17/sec
----------------------------
To Defend Forward, US Cyber Strategy Demands a Cohesive Vision for Information Operations
By The Honorable Patrick J. Murphy | Dr. Erica Borghard | November 18, 2020
PRINT
In 2018, the United States (US) Department of Defense (DoD) published the 2018 Cyber Strategy summary featuring a new strategic concept for the cyber domain: defend forward. It states DoD will, “defend forward to disrupt or halt malicious cyber activity at its source, including activity that falls below the level of armed conflict.”[1] This reflects an important shift in DoD’s strategic posture, compared to the 2015 Cyber Strategy, in two key ways.[2] First, defend forward rests on the premise that to deter and defeat adversary threats to national security, the US could not solely rely on responding to malicious behavior after the fact. Rather, the DoD should be proactive in maneuvering outside of US cyberspace to observe and understand evolving adversary organizations and, when authorized, conduct operations to disrupt, deny, or degrade their capabilities and infrastructure before they reach the intended targets. Implied, but not explicitly stated, in the 2018 strategy summary is the role of information operations, and the relationship between cyberspace and the information environment. According to US doctrine, the former is a subset of the latter.[3] This article builds on our work as members of the US Cyberspace Solarium Commission to offer a conceptual framework and policy recommendations for integrating information operations in the context of defend forward. Many of the Commission’s 82 recommendations are slated to pass in the Fiscal Year 2021 National Defense Authorization Act (NDAA).
https://cyberdefensereview.arm....y.mil/CDR-Content/Ar
------------------------------
Here’s how Cyber Command is using ‘defend forward’
Mark Pomerleau
November 12, 2019
U.S. Cyber Command is using new authorities to gain insights and access to foreign networks to help better inform defense. (U.S. Cyber Command Public Affairs)
U.S. Cyber Command is gaining important insights into malware and adversarial actors by working with partner nations to help secure their systems, according to a top official.
“We’re also working with our partners, participating in defending U.S. critical infrastructure from malicious cyber activity,” David Luber, executive director of Cyber Command, said at CyberCon 2019. “That’s where we have a chance to see what our adversaries are doing in cyberspace because we now have the authority under the National Defense Authorization Act 2019 to operate outside the DoD networks to help our allies defend forward. That’s a big difference, because in the past the DoD could only operate in its own networks. But, when invited by our allies, we can now work and help defend inside of their networks.”
This action is what the Department of Defense calls “defending forward,” or getting as close to adversaries as possible to see what they’re planning as a means of informing others to prepare or take action themselves.
Two years later, what does persistent engagement and defend forward mean? (Patrick Semansky/AP)
Two years in, how has a new strategy changed cyber operations?
This is the story of how, in two short years, a new cybersecurity strategy has forced the national security community to rethink cyber operations and how "persistent engagment" will work.
Mark Pomerleau
“We’re seeing some very interesting malware and other activities when we conduct some of those defend-forward missions,” Luber said. “Then we take that information and we share that broadly with industry and the rest of the government.”
Moreover, Luber added, part of Cyber Command’s goal is to make sure they have the opportunity to be in foreign cyberspace to be able to conduct operations to counter threats.
In cases in which Cyber Command defensive teams were invited to help defend networks of other nations, such as Macedonia, Ukraine and Montenegro, the command learned a lot about malware.
“They invited us in to work with them within their networks in a defensive role and then we gleaned some tremendous insights into advanced persistent threats and malware and were able to bring that to the world through publishing on websites,” he said.
Sign up for our Daily Brief
Get the top Cyber headlines in your inbox every weekday morning.
Enter your email address
(please select a country)
Subscribe
Additionally, Luber emphasized, the importance of constantly sharing information between government and industry was shown throughout operations to help defend the 2018 midterm election.
“By streamlining some of those policy issues by working closely with DHS and FBI, we were able to get indicators of compromise directly down to industry very quickly,” he said.
https://www.fifthdomain.com/sm....r/cybercon/2019/11/1
--------------------------
https://www.itcentralstation.c....om/products/comparis
----------------------
There are so many ways to (CONVERSATION) with your EMPLOYEES the [Governed] Qballs~ /_\ Slave Government of your home town to the U.N. FLAGS.......,
and ask them why FREE MASON (Lodges) make all the LAWS in the USA.?.?.?
The Society of nonmaosn~ #TheCrewRRR [{**}]
https://www.usa.gov/elected-officials/
-------------------------
I never knew it was so hard to get the PUBLIC Email: for our Public Employed FREE MASON Local Officials from Mayors - Governors - Presidents to what not.?.?.?
I mean if you call, you got too leave a message, but if you EMAIL your local official it is a LEGAL Writ, and it must be (upheld) in a Court of LAW......., so I guess you just gonna have to write a {Real Letter} +=+ to these U.N. Troops of {G4S] and all their FREE MASON C.O.P.S.
all whom live like {Kings and Queens} off of your PUBLIC PAID TAXES TAXES TAXES......., and yet we the nonmason Gentile POPULATIONS [got no say] QBALLS~ /_\ in the LAWS that take us away from our loved ones????
https://www.shelby.senate.gov/public/
----------------------------
Now if you want too look into JOBS at G4S you can find them on this web page...
The Rag Tag Rebellion "of and for" OUR WORLD REPUBLIC CONSTITUTION Coalition...
The Society of nonmason~ #EXODICE [{**}]
https://www.g4s.com/contact-us/call-or-email-us
----------------------
So I get in, and there is NO .pdf to Download.... Oh Well, we know how this Game of Purgatory Works...
The Sentinel~ #TheCrewRRR [{**}]
Best Digital Risk Protection Solutions
Over 472,704 professionals have used IT Central Station research.
Compare the best Digital Risk Protection vendors based on product reviews, ratings, and comparisons. All reviews and ratings are from real users, validated by our triple authentication process.
https://www.itcentralstation.c....om/categories/digita
----------------------